Metaverse security took a big step forward today as Avination donated OpenSim code implementing an “export” permission setting. The company also worked together with Singularity viewer developers to add support for this new permission to the viewer.
Today, OpenSim has three permissions — copy, transfer, and modify — that determine what users are able to do with their content. However, there is no permission setting for exporting content out a grid because the permissions were inherited from Second Life, which does not allow this functionality.
OpenSim, however, has three ways in which users can export content — OAR exports which save everything physically located on a region, IAR exports which save a user’s entire inventory, and hypergrid teleports which allow content to be carried from one grid to another. In addition, people who run their own OpenSim servers can give themselves “God powers” that allow them to change existing permission settings.
To keep content safe, commercial grids prohibit their users from connecting regions run on home-based OpenSim servers, disallow “God powers,” don’t offer OAR or IAR exports, and turn off hypergrid teleports.
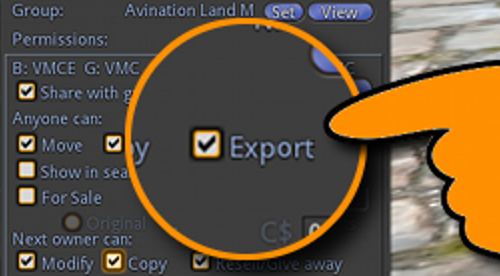
The new “export” permission setting will allow grid owners to configure their grids so that only exportable content can leave via hypergrid teleport, or via OAR or IAR exports.
As a result, commercial grids will be able to offer hypergrid connectivity and backups to their users and, as long as “God powers” are prohibited, still be able to protect proprietary content.

“The code will be released ‘as we go,'” Avination grid founder and OpenSim core developer Melanie Thielker told Hypergrid Business. “People will be able to see, comment and improve on it while we work. Other viewers can extract the code from the Singularity code base, which is, of course, open source, and integrate this feature.”
Avination has donated code to OpenSim before, most recently the multi-attach feature. Typically, however, donations by commercial grids come after enough time has passed for the grid to profit from its own invention.
That is not the case this time, said Thielker.
“There will be no delay between the development and the release to OpenSim core,” she said. “This feature is an important milestone and should go out there without delay. We recommend that viewer developers wait a few weeks before taking code from Singularity because the viewer side still needs debugging — as does the server side.”
Although creators will need to use Singularity or another viewer which adds the code in order to set the “export” permission, the permission will still be in effect even if the eventual purchaser of the content uses a different viewer.
Attempts to export non-exportable items will have no effect, just as if the user had attempted to copy a no-copy item, or modify a no-modify item. The viewer simply allows the user to see what the setting is, or change the setting if they are a creator — the actual decision to allow the export or not will take place on the server.
The export flag not only allows users to take some content from one grid to another, but also to have the same appearance wherever they go.
Creators who allow the “export” functionality on some of their items will be able to see their brands spread throughout the hypergrid, the company added.
The new export permission will not keep determined hackers from stealing content, however. Various tools and methods are in use in Second Life, for example, where the much larger array of available content makes it an attractive target for content thieves.
The new export permission code will become part of the OpenSim core code, Avination said in its announcement today.
OAR and IAR export checking are not part of the donated code base, however. Adding export permission checking will be up to other developers, said Thielker, who work on that part of the code.
Similarly, the code donated today does not address the issue of saving objects as XML files.
“The viewers do their own permissions checking,” she said. “Viewers with export functionality could implement support.”
The most popular viewer today for XML object exports is Imprudence, but that viewer is no longer actively supported.

OpenSim core developer Justin Clark-Casey, who also heads up the Overte Foundation that manages OpenSim development, suggested that other viewers either wait for the work to be complete, or actively work with Singularity and Avination on the development.
Those interested in finding out more, or in contributing to the effort, can follow the OpenSim developers mailing list, or check in on the OpenSim Developers chat channel, he added.
“This is a work-in-progress,” he said.
Changes in licenses
Today, there is a default, implied content license associated with the OpenSim permissions system. Users are allowed to transfer some items but not others, copy some times, modify some items, and these rights can come in any combination.
And, by default, all content is licensed only for its grid of origin, unless the creator specifically steps up and says otherwise — say, in an attached notecard.
The new permission setting comes with a new implied license.
“Exportable items can be taken to any grid without worrying about licensing issues because an item marked as exportable means that the creator has licensed the item under a permissive open license that allows use of the item anywhere,” the announcement said. “Exportable items can be taken to any grid and can be given, traded and sold as the current owner sees fit, without any royalties and without violating any laws.”
As a result, items that can be exported become, in effect, transferable and copyable.
This may be due to the fact that with export allowed, users can take content to a grid where they have “God powers” and then change any permission setting they want.

But this view of the export permission could also cause some confusion, said Kitely CEO Ilan Tochner.
“AÂ permissive content license shouldn’t be forced on merchants or very few of them will agree to sell items this way,” he told Hypergrid Business. “I think that Copy, Modify, and Transfer permissions should continue working as they do now even when an item is brought over via hypergrid.”
Someone who uses “God powers” to break those permissions would be guilty of breaking copyright law, Tocher said. This would be the same as if someone had use another hacking tool to, say, “copybot” an item.
“It would be very bad for the metaverse if people associate allowing content to have Export permission with the content creator losing control of what can be legally done with their creations,” Tochner said.
Kitely is currently implementing its own export permission as part of its Kitely Marketplace. Kitely has also donated code to the OpenSim community that allows grid owners to filter OAR exports so that, say, users can only save content they themselves have created, or only full-perm content.
According to Thielker, there is no way to control what happens to content after it leaves the grid, and letting creators think so would give them a false sense of security.
“Grids may not have any permissions, or allow any region owner to zap permissions, like OSgrid,” she said. “It must be understood from the start that permissions restricting the use of an item are plainly unenforceable once grid borders are crossed. Therefore our implementation requires the items to be set to full perm before the export flag can be set.”
Creators who want to set further restrictions can do so in the form of an attached license, she said.
“And the current state of the metaverse shows clearly how much store people set by such licenses,” she added. “This is why allowing normal permissions on an exportable item is a sham that will lead to disappointed creators, irate users and possibly lawsuits against the grid operator.”
Securing hypergrid access
In addition to keeping proprietary content in, some grid owners are also concerned with keeping hypergrid travelers out, particularly griefers and hackers.
Currently, there are few options available.

“Grid operators can restrict hypergrid visitors based on their grid of origin,” said hypergrid inventor Crista Lopes, professor of informatics at the University of California, Irvine.

And grids can turn off hypergrid access altogether.
“But I am planning to restart working on access control very soon,” Lopes told Hypergrid Business.
Turning off hypergrid access to a single grid in order to deal with a small number of griefers can cause significant public relations problems for a grid, as has recently happened with OSgrid, as innocent people get caught in the ban.
- International singers gather on Alternate Metaverse Grid for first annual International Day - April 15, 2024
- OpenSim hits new land, user highs - April 15, 2024
- Wolf Territories rolls out speech-to-text to help the hearing impaired - April 15, 2024
